in the authorization server since it is authroization_code grant type
we need to specify redirect url in ClientDetails
public class SecurityClient implements ClientDetails {
private final Client client;
public SecurityClient(Client client) {
this.client = client;
}
@Override
public String getClientId() {
return client.getClientId();
}
@Override
public boolean isSecretRequired() {
return true;
}
@Override
public String getClientSecret() {
return client.getSecret();
}
@Override
public boolean isScoped() {
return true;
}
@Override
public Set<String> getResourceIds() {
return null;
}
@Override
public Set<String> getScope() {
return Set.of(client.getScope());
}
@Override
public Collection<GrantedAuthority> getAuthorities() {
return List.of(() -> client.getScope());
}
@Override
public Set<String> getAuthorizedGrantTypes() {
return Set.of(client.getGrantType());
}
@Override
public Set<String> getRegisteredRedirectUri() {
return Set.of("http://localhost:9090");
}
@Override
public Integer getAccessTokenValiditySeconds() {
return null;
}
@Override
public Integer getRefreshTokenValiditySeconds() {
return null;
}
@Override
public boolean isAutoApprove(String s) {
return false;
}
@Override
public Map<String, Object> getAdditionalInformation() {
return null;
}
}
we are getting client from database and warp it with SecurityClient

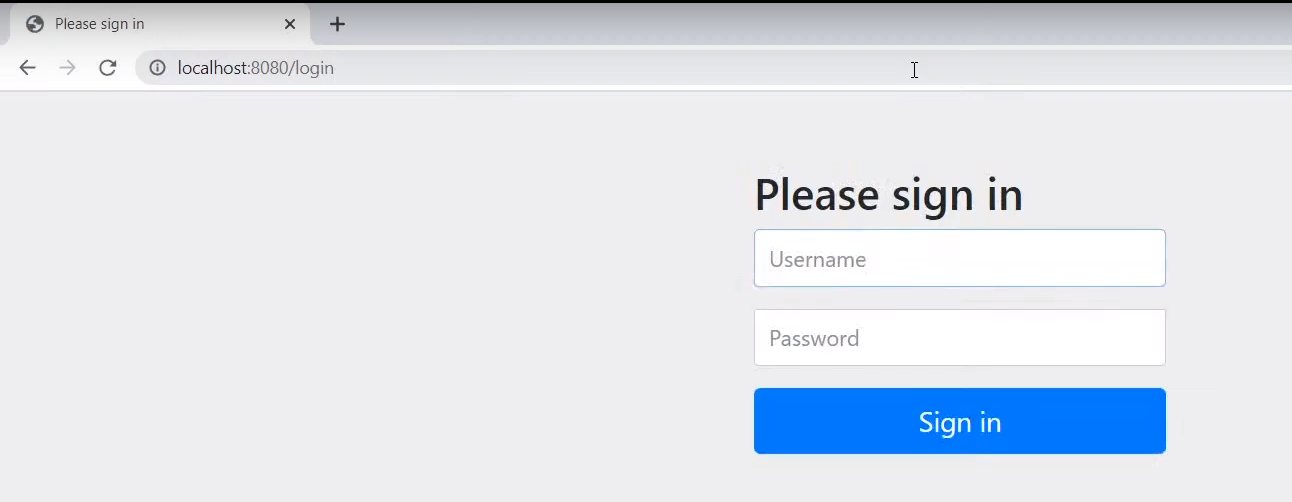
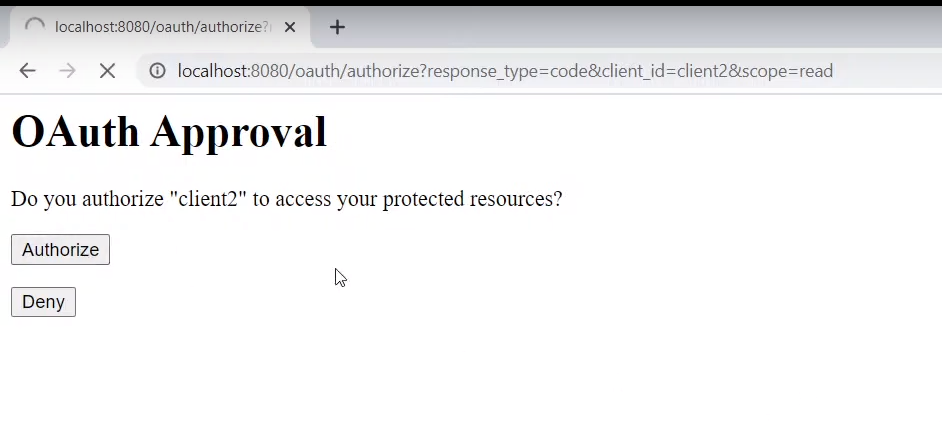

user tries to access Authorization server -> require user's credential -> confirm it and ask user if user is going to allow client to use some resource -> authorization gives authorization_code and go to given redirect url

notice we can get access token without user's credential since it is authentication_code grant type

if we try to authorization_code more than once it will be rejected
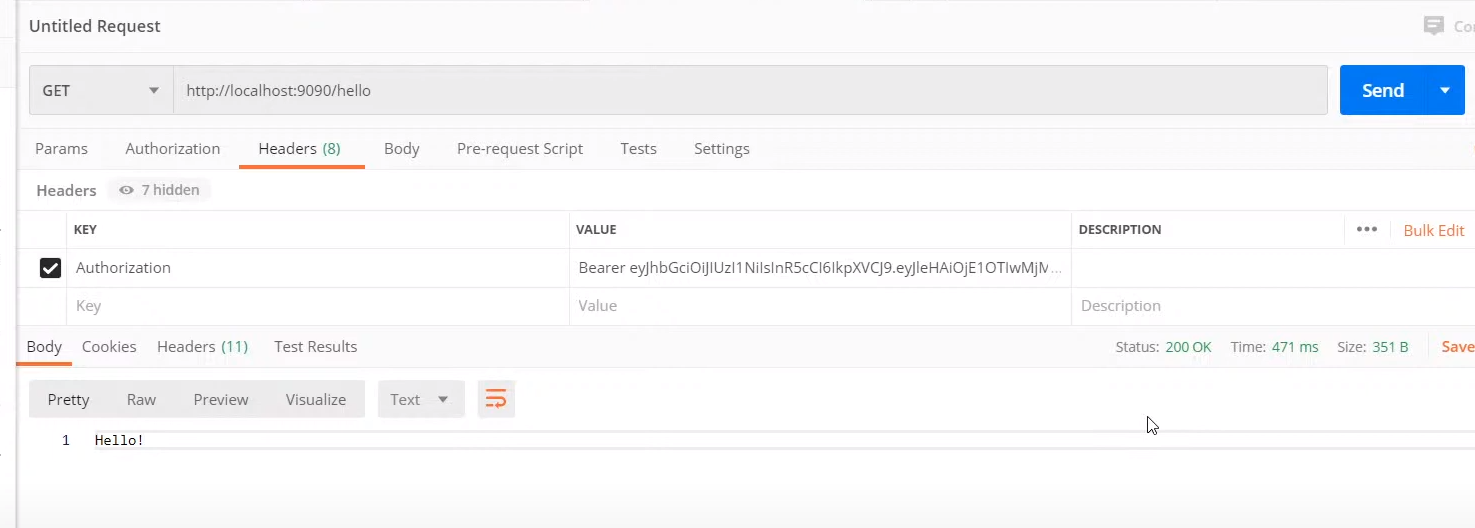
with given access_token (in this case JWT) -> we can access resource server

this is our case, authentication server and resource server having same key
but this is not recommanded because resoruce server can not only validate but sign the JWT

first command is to generate private key -> gives you ssia.jsk file , with password "ssia123"
second command is to generate public key with given private key at the first command
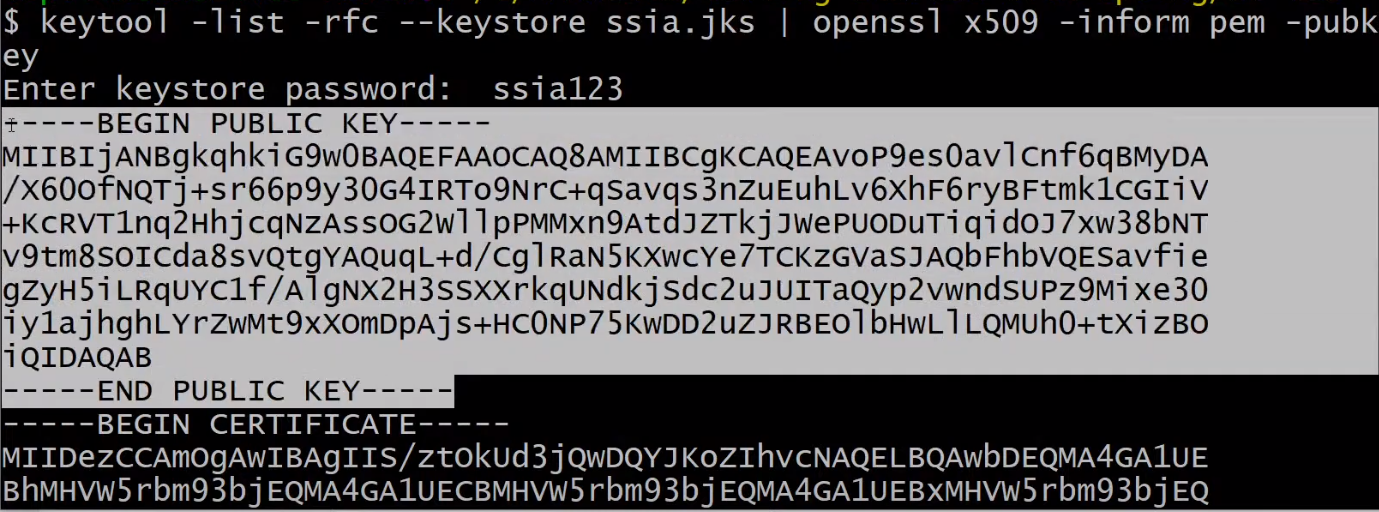
resource server will vadliate with this public key which is key pair of authentication server's key pair
@Bean
public JwtAccessTokenConverter converter() {
var conv = new JwtAccessTokenConverter();
KeyStoreKeyFactory keyFactory =
new KeyStoreKeyFactory(
new ClassPathResource("ssia.jks"),
"ssia123".toCharArray()
);
conv.setKeyPair(keyFactory.getKeyPair("ssia"));
return conv;this is for authentication server
@Value("${key}")
private String publicKey;
@Bean
public TokenStore tokenStore() {
return new JwtTokenStore(converter());
}
@Bean
public JwtAccessTokenConverter converter() {
var conv = new JwtAccessTokenConverter();
conv.setVerifierKey(publicKey);
return conv;
}
for resource server , getting public key from app.properties
'WEB > Security' 카테고리의 다른 글
| Lesson 20 - Using Keycloak as an authorization server (0) | 2022.05.11 |
|---|---|
| Lesson 19 - Configuring the authorization server to expose the public key (0) | 2022.05.11 |
| Lesson 16 - Using non-opaque tokens in Spring Security with JWT (0) | 2022.05.10 |
| Lesson 15 - Using Opaque Tokens - Blackboarding (0) | 2022.05.09 |
| Lesson 14 - Using Opaque Tokens - Introspection (0) | 2022.05.09 |