https://tonylim.tistory.com/280?category=938556
OAuth 2.0 and OpenID Connect (OAtuh 2.0 in depth)
https://www.youtube.com/watch?v=996OiexHze0&t=96s&ab_channel=OktaDev History basic security from has some downsides on security and maintenance OAuth 2.0 terminology Resource owner = me , who owns..
tonylim.tistory.com
https://tonylim.tistory.com/149?category=938556
[java brains] OAuth2 , Google
oAuth = Authorization between services only giving other service with limited credential. once user permit different service to access google OAuth gives a token with limited access authorites wri..
tonylim.tistory.com
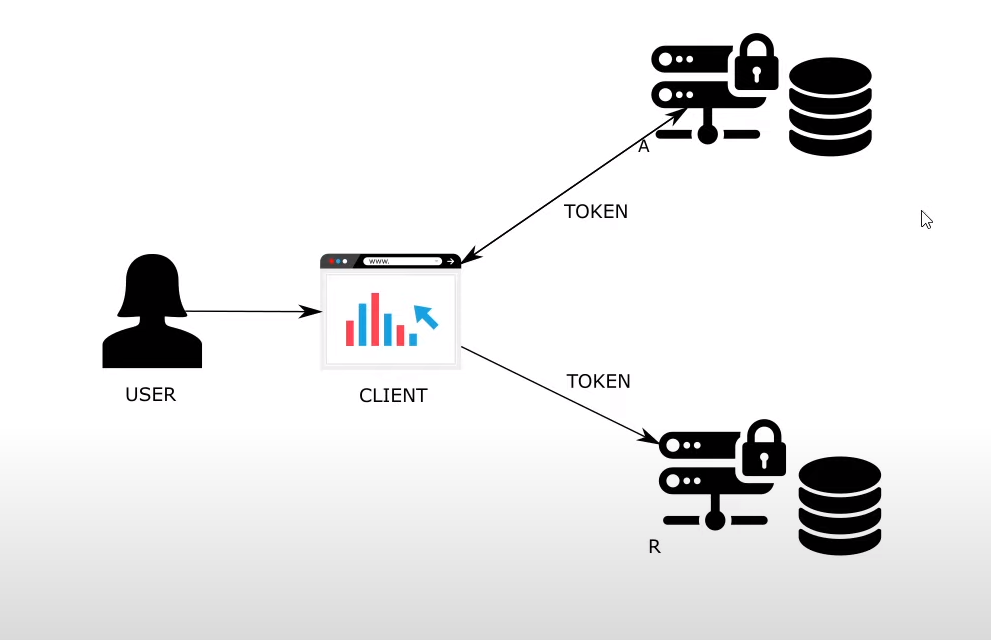
2things that authorization server needs to know
1. user information -> managed by UserDeatilService in

2. client information managed by

seperate representation for client and user.
authenticationMangaer links between client and user authentication (not sure what this mean)
similar to UserDetailService -> clients.InMemory == InMemoryDetailsManager
5 grant Types in oauth -> way client get authorized token
1. authoriziation_code
2. password == deprecated -> what we are using now
3. client_credenitals
4. refresh_token
5. implicit == deprecated (no one use it)
Creating filter chain: OrRequestMatcher [requestMatchers=[Ant [pattern='/oauth/token'], Ant [pattern='/oauth/token_key'], Ant [pattern='/oauth/check_token']]]

notice with passing password(credential) -> 3 party knows credenital which is dangerous
but it is simple

this request is for client1 (password grant type)
client send user's id and password to /oauth/token -> get access token
user calls cllient to use some feature -> client redirects user to authorization server ->
user authenticate to authentication server with username and password -> client receive authroization token from server by given redirect url(go back to client)
this is implict grant type which is deprecated
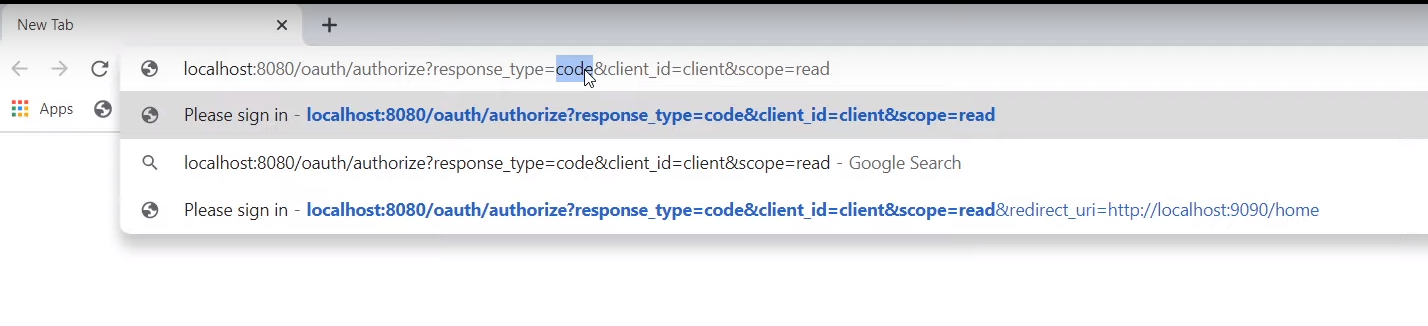
client send request = code means we will use authorization_code (difference from implicit)

client redirects user to loginForm which our authenticaiton Server gave (just like google form)

user authorize client2 use some resources

authentication server gives authorization code to client with given redirect url

we send code(authorization code) to get acutal access token from authentication server

if we request one more time with same code it gives us error , we need to authenticate again or use refresh token
'WEB > Security' 카테고리의 다른 글
| Lesson 13 - Token implementations in OAuth 2 systems (0) | 2022.05.09 |
|---|---|
| Lesson 12 - Deeply understanding the grant types (0) | 2022.05.06 |
| Lesson 10 - (Cross-Origin Resource Sharing) CORS (0) | 2022.05.06 |
| Lesson 9 - (Cross-Site Request Forgery) CSRF (0) | 2022.05.06 |
| Lesson 8 - The Security Context (0) | 2022.05.06 |