
&etext = points to first address of code section.
&edata = points to initialized data section.
&end = points to bss section
brk = points to top of heap all the time. , when program is started &end , brk points to same address


page size is 4kb
address of main is below to &etext address.
Initialized var is below &edata.
uninitalized var is bleow &end.
ii is address of heap which is above &end.
rest of belows are stack variable it will keep change randomly when we execute ./a.out , it is for security reason. we can disable randomization by "echo 0 | sudo tee /proc/sys/kernel/randomize_va_space".

argc tells how many words are in command line argument.
notice in index 0 program name is passed.

we can take advantage of that by compiling our program with different name.
to display env variable "set | less" will do.
Reasons to modify the env variables
- to build a suitable environment for a process to run.
- a form of IPC(Inter process communication) , since a child gets a copy of its parent's environment variables at the time it is created.
with "getenv" , "putenv" , "setenv" , "unsetenv" , "clearenv" we can manage env variables.
Function Stack Frame

to store local variables , passing arguments to the functions, store return address, base pointer.
rbp = frame pointer
rsp = stack top
rip = return address
rbp block is containing starting address of "main" stack frame is saved on stack for alter use, and rbp pointer is moved to where rsp is pointing , to create new stack frame pointe rof function foo()


after foo() function exectues return. memory on the stack is freed automatically.
saved base pointer i spoped an dplaced in rbp , which moves to starting address of main FSF
saved return address is popped and place in rip (return)
stack is shrinked by moving rsp further up to where rbp is pointing.
Buffer Over Flow
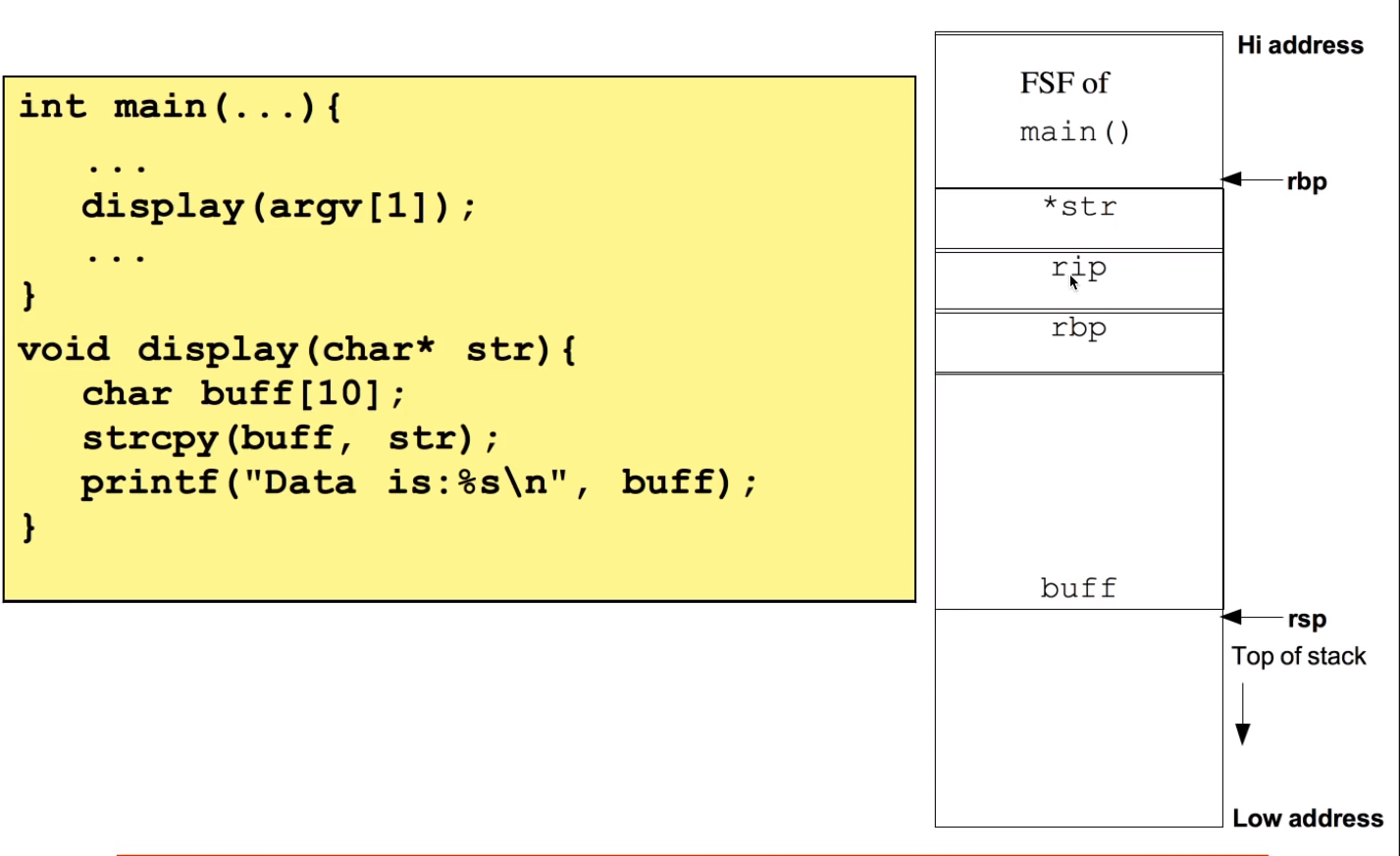
when str is larger than char buff[10] it will override rbp ,rip block and so on. which will cause "segmentation fault".
jump


at first encounter of setjmp it will state of stack will be save in envuf variables and return 0.
it will go if block and execute func and meet longjmp function.
longjmp will goto envbuf state and will encounter setjmp for the second time and return 52 not 0.
so it won't go to if block.
'Operating System > System Programming(Arif Butt)' 카테고리의 다른 글
| Lec11) Design and Code of UNIX more utility (0) | 2021.06.25 |
|---|---|
| Lec10) Heap Behind the Curtain (0) | 2021.06.23 |
| Lec08) Exit Handlers and Resource Limits (0) | 2021.06.18 |
| Lec 6, 7) Versioning Systems git-1,2 (0) | 2021.06.15 |
| Lec05) GNU autotools and cmake (0) | 2021.06.13 |